OHSINT
For complete tryhackme path, refer the link
Tools Used
- Exiftool
- Wigle.net
Task 1 - OhsINT
Download the image and read the embedded information in it.
exiftool /data/WindowsXP.jpg
We see GPS coordinates, and user information from copyright.
ExifTool Version Number : 11.16
File Name : WindowsXP.jpg
Directory : /data
File Size : 229 kB
File Modification Date/Time : 2020:12:22 02:27:01+05:30
File Access Date/Time : 2020:12:22 02:27:22+05:30
File Inode Change Date/Time : 2020:12:26 03:45:44+05:30
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
XMP Toolkit : Image::ExifTool 11.27
GPS Latitude : 54 deg 17' 41.27" N
GPS Longitude : 2 deg 15' 1.33" W
Copyright : OWoodflint
Image Width : 1920
Image Height : 1080
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
GPS Latitude Ref : North
GPS Longitude Ref : West
Image Size : 1920x1080
Megapixels : 2.1
GPS Position : 54 deg 17' 41.27" N, 2 deg 15' 1.33" W
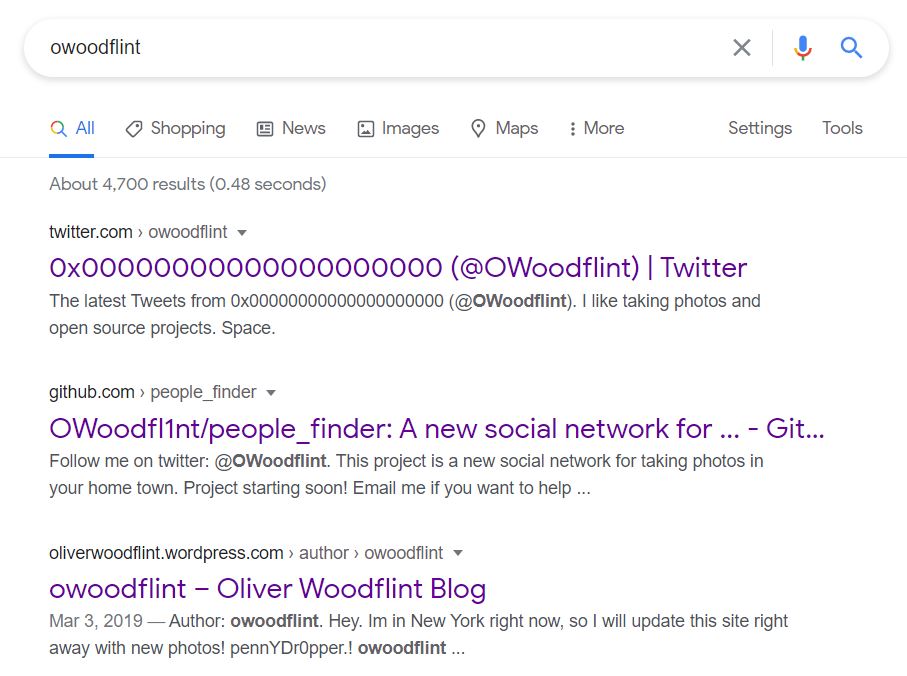
A google search on owoodflint gives twitter, github and wordpress results in the top 3 search results.
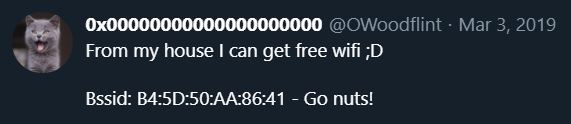
The image in Twitter url is first flag.
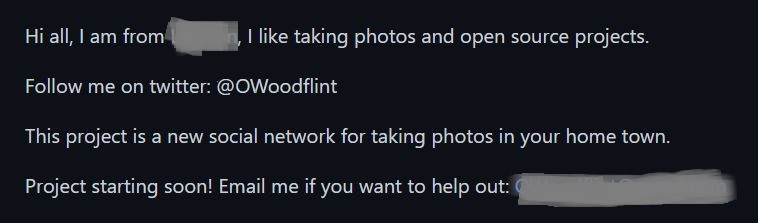
The information in GitHub url shows a location, which is second flag, and a mail id, which is fourth flag. The source of this information is fifth flag.
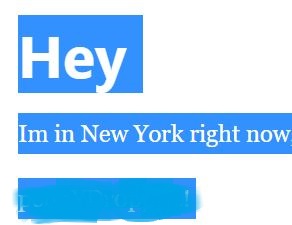
The Wordpress url shows a holiday location, which is sixth flag.
The seventh flag is the most tricky part. Select all contents in the Wordpress url, which will reveal a hidden text, aka., the seventh flag.
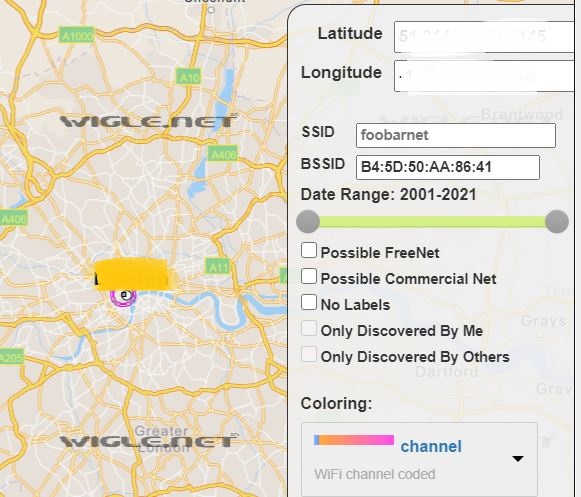
To get third flag, check the remaining clue, the GPS coordinates, in the link. As we got the MAC address from twitter, and location in GitHub, we can search for BSSID in the wigle url, and see if there is a result in location.
Zoom in fully to get the BSSID of the MAC address, which is the third flag.